Managing machine identities in a zero-trust world
Enterprises are struggling to manage the proliferating machine identities their organizations create. Existing methods are not scaling to secure them.
The typical enterprise has 45 times more machine identities than human ones — and many organizations don’t even know exactly how many they have. More than six in 10 enterprises are unsure of their organization’s key and certificate count, up 17% from last year.
That’s why it’s so difficult for many CISOs to get control of their machine identities. The typical enterprise had 250,000 of them to manage in 2021, projected to double to 500,000 by 2024.
Ponemon Institute’s third annual State of Machine Identity Management report, published by Keyfactor, provides an accurate glimpse into the current state of machine identity management — and why zero trust is critical to getting it right.
Event
CISOs tell VentureBeat that managing the huge number of machine identities created by applications, containers, cloud services, scripts, virtual machines (VM), and mobile and laptop devices is the most challenging part of getting the identity and access management (IAM) aspect of zero-trust frameworks right.
Adding to the challenge is the need to manage machine identities’ lifecycles.
Starting with an enterprise-wide strategy for public key infrastructure (PKI) infrastructure management is core to the effort.
How machine identity management supports zero trust
A combination of factors is increasing the urgency of getting PKI right as a core part of an enterprise’s machine identity management (MIM) strategy: Enterprises are pursuing zero-trust frameworks. They are expanding their IoT networks. And they are pursuing more cloud services.
But CIOs and CISOs tell VentureBeat that their teams are already stretched thin, while PKI infrastructure is getting more complex as machine identities grow. Pulled in two directions, IT and cybersecurity teams are having a harder and harder time keeping up.
“A PKI infrastructure certificate is simply a validation of an identity to a system. It’s looking at a system and saying, ‘I’m giving you a certificate as proof of your identity’ … When that certificate is presented, it’s essentially asking for access to a resource,” Kapil Raina, vice president of zero trust, identity, and data security marketing at CrowdStrike, told VentureBeat during a recent interview.
CrowdStrike has implemented its identity segmentation to adhere to the NIST SP800-27 zero trust architecture standard. “The idea of identity segmentation does exactly that. We rely on identities to define the zones where our customers want to limit lateral movement or the damage,” Kapil said.
To help organizations take on this challenge, identity and access management (IAM) platforms need to keep improving machine lifecycle management tools for applications, customized scripts, containers, VMs, IoT, mobile devices and more. Leading vendors in this area include Akeyless, Amazon Web Services (AWS), AppViewX, CyberArk, CrowdStrike, Delinea, Google, HashiCorp, Keyfactor, Microsoft and Venafi.
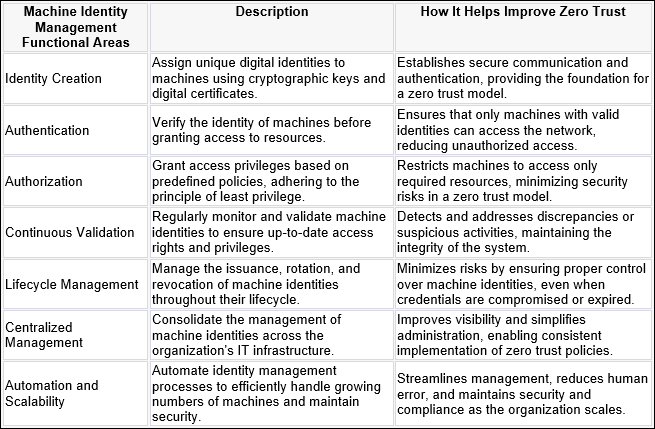
Enforcing least privileged access and strengthening how every machine’s identity is validated in real time enables machine identity management to become a cornerstone of any zero-trust security framework. Comparing how MIM’s functional areas help improve zero trust underscores why taking a lifecycle-based view of machine identities and getting in control of key management are core to strengthening a zero-trust security framework enterprise-wide.
Managing machine identities is a multifaceted challenge
Another factor that makes it challenging for CISOs to excel at managing machine identities is the diverse needs of DevOps, cybersecurity, IT, IAM and CIO teams. Each has its own tool and application preferences. Yet CIOs tell VentureBeat that cross-functional teams are critical to balancing centralized governance and operational functionality.
Getting senior management and, ideally, a C-level executive to own the problem is essential to progress. The good news is that senior management is stepping up and taking ownership. Thirty-six percent of enterprises said lack of executive support was a serious issue in 2021. That dropped to 22% last year.
Ponemon found that CIOs are facing new, more complex challenges protecting their rapidly proliferating machine identities. The following are the critical insights gained from Ponemon’s latest report:
PKI for IoT and DevSecOps are among the fastest-growing use cases today
Securing hybrid and multicloud configurations as part of the broader tech stack requires PKI to protect the many new machine identities created daily. Many are ephemeral or used for a relatively short period, making an automated approach to PKI for container and VM creation table stakes for staying consistent with a zero-trust strategy.
The study found that DevSecOps and IoT environments have increased in importance as leading trends driving increased adoption of PKI infrastructure. IoT’s importance as a top trend increased from 43% in 2021 to 49% in 2023. DevSecOps’s rose from 40% in 2021 to 45% this year.
Improving zero trust requires getting control of certificate authority (CA) and PKI sprawl
From internal CAs and self-signed certificates to cloud-based PKI and CAs built into DevOps tooling, PKI permeates larger-scale enterprises. According to survey respondents, the average enterprise uses nine CA and PKI solutions.
In 2023, machine ID management teams prioritized reducing PKI infrastructure complexity to regain control and prevent the spread of non-compliant and untrusted CAs. Getting CA and KPI sprawl under control is a must for improving zero-trust security postures across an enterprise.
CISOs face difficulty hiring PKI experts, and many are short-staffed already
Labor shortages hurt PKI and machine identity strategy for CISOs and security teams. Respondents say their teams’ most significant challenges are 1) lacking skilled workers and 2) too much change and uncertainty. Fifty-three percent of respondents, up from 50% in 2022, say they lack the staff to deploy and maintain their PKI.
KPI certificates are being created faster than existing systems can track
Internally trusted certificates (i.e., certificates issued from an internal private PKI) increased for the third year in a row, from 231,063 in 2021 to 255,738 in 2023. PKI teams are struggling to manage these increasing numbers of certificates; 62% of respondents don’t know how many keys and certificates they have, up from 53% in 2021.
Outages caused by certificate expirations are happening more often, impacting customer relationships
Applications and services stop working if certificates expire unexpectedly. For 77% of respondents, at least two such incidents occurred in the past 24 months. Fifty-five percent of respondents said certificate-related outages severely disrupted customer-facing services. And half say these events caused significant disruption to internal users or a subset of customers.
Machine identities are core to zero trust
The fastest growing threat surface in many organizations today comes from the thousands of machine identities being created by implementing new IoT networks, expanding cloud services, and creating new containers and VMs to support Devops and DevSecOps.
Getting in front of this reality at scale is a challenge facing CIOs and CISOs, who often lack a PKI expert on staff or a person available to dedicate to the process full-time.
To improve its zero-trust posture, any organization needs to start by taking a more data-driven approach to managing PKI infrastructure and machine identities at scale.